How To: Provide read and write access to Application Pool Identities
Application Pool Identities are an effective new isolation concept innovated for Windows Server 2008 and later versions of Windows. An application pool identity allows you to run an application pool under a unique account without having to create and manage domain or local accounts. The name of the application pool account corresponds to the name of the application pool. AppPool Identities make IIS applications even more safe and dependable.
In IIS 6.0 and IIS 7.0, worker processes run as Network Service by default. Network Services is a relatively low-privileged account and is a built-in Windows identity. It is wise to run a low-privileged account as a security best practice to reduce soft targets for malicious software bug.
However GINESYS recommends running IIS 7.5 or a later version of IIS on Windows Server 2008 R2 or later OS. For the aforementioned versions, users don't require to do anything to use the new identity. For every application pool created, the Identity property of the new application pool is set to ApplicationPoolIdentity by default. The IIS Admin Process (WAS) creates a virtual account with the name of the new application pool and run the application pool's worker processes under this account by default.
Important information
An Internet Information Services (IIS) worker process is a windows process(w3wp.exe) which runs Web applications, and is responsible for handling requests sent to a Web Server for a specific application pool.
On creation of a new application pool, a security identifier (SID) is created by the IIS management process. This SID takes on the name of the application pool itself. To exemplify, for an application pool with the name MyNewAppPool; a security identifier with the name - MyNewAppPool is created in the Windows Security system. From this point on, this identity can be used to secure resources. However, the identity will not show up as a user in the Windows User Management Console; as it is not a real user account.
Step-by-step guide
After the App Pools are created and applications have been mapped to it, read and write rights need to be given to the App Pool identities / Virtual users. Follow the steps given below for it:
Open the IIS.
Expand the view to the mapped applications.
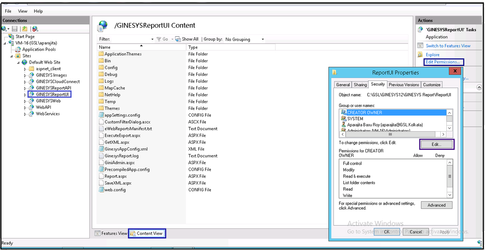
In the Content View tab, Actions section, click on Edit Permissions.
In the Properties window, select the Security tab.
In the Security tab, click Edit button.
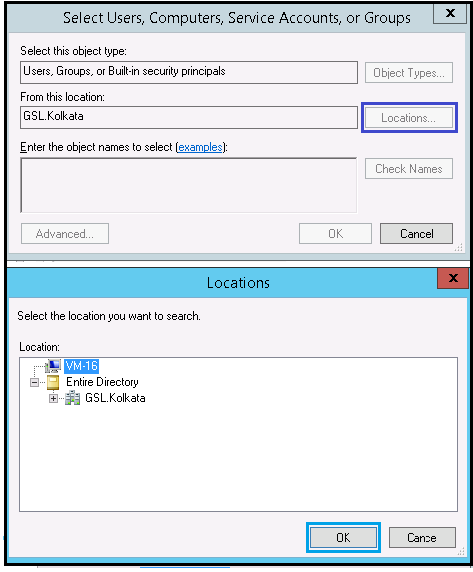
In the Permission for <folder name> window, click the Add button.
In the Select Users, Computers, Service Accounts, or Groups;
By clicking the Location button, select <Computer Name> in the Locations window
In the object names, type Users in the text box and click on Check Names. Once you find the name - IIS_IUSRS in Search Results, click on OK.
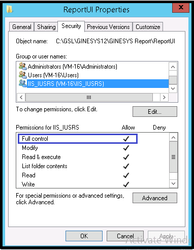
Now in Security tab, select IIS_IUSRS provide Full Control by ticking the checkbox. Then click on Apply and OK.
In the Permission for <folder name> window, click on OK.